Automation in Retail: From Inventory to Checkout
Retail has always been about getting products into customers’ hands quickly and efficiently. Today, automation is taking that idea to a whole new level. From the moment goods arrive at a store or warehouse to the second a customer pays, technology can now manage nearly every step.Continue Reading
How Firewall Works in Computer Network?
In today’s rapidly evolving digital landscape, cybersecurity is more critical than ever. One of the most vital components of securing a computer network is the firewall. Firewalls are crucial for safeguarding sensitive information and ensuring the integrity and security of private networks. This article explores in-depth how a firewall functionsContinue Reading
How to Change SD Card in Android Without Losing Data (Photos, Videos & More)
An SD card is a crucial storage component for many Android users, allowing them to store photos, videos, apps, and other important files. However, replacing an SD card can be challenging, especially if you want to keep your data safe. Changing an SD card in an Android device without losingContinue Reading
iPhone Not Working Without WiFi? Top Reasons & Solutions
Having an iPhone that does not work without WiFi can be frustrating, especially when you rely on mobile data for connectivity. This issue can stem from several causes, including software glitches, incorrect network settings, SIM card issues, or carrier-related problems. By the end, you’ll have a better understanding of whyContinue Reading
Essential Gear for Today’s Digital Workplaces
As technology continues to evolve, so does the nature of how we work. Digital workplaces have become a staple for many businesses, enabling employees to work remotely, collaborate across distances, and access tools that enhance productivity. To make the most of this digital revolution, it’s important to invest in theContinue Reading
How Does Ransomware Spread Through a Network: Key Factors and Prevention Tips
In the field of cybersecurity, ransomware has become one of the most deadly types of malware. It is designed to encrypt files on a victim’s device, making them inaccessible until a ransom is paid. Ransomware has the ability to quickly spread across networks in addition to individual devices, affecting entireContinue Reading
What is a Decentralized VPN? How They Work and Why You Need One?
Peer-to-peer networks and blockchain technology are used by dVPNs to deliver a more secure, transparent, and censorship-resistant surfing experience than regular VPNs, which rely on centralized servers run by a single provider. But what exactly is a decentralized VPN, how does it work, and can it truly outperform traditional VPNs?Continue Reading
Why and How To Convert SQL Server to MySQL
MySQL and SQL Server are hard to compare. Each of these DBMS has its own cons and pros and can handle huge, complicated data databases requiring safe simultaneous access. However, numerous organizations intend to migrate their databases from SQL Server to MySQL in order to use the following advantages: AffordableContinue Reading
Ways To Find Lost AirPods [Step-by-Step Guide]
Losing your AirPods can be frustrating, especially when they’re tucked away in some unseen corner. However, Apple has implemented several methods to help you find your lost AirPods quickly. The Find My app is a powerful tool that shows the last known location of your AirPods on a map. ThisContinue Reading
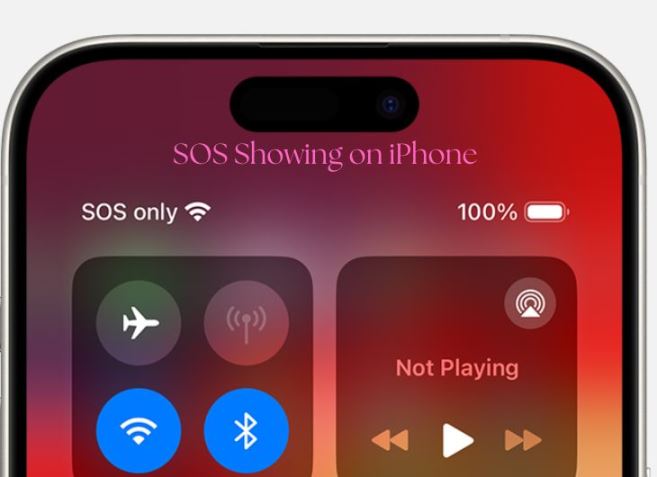
Why is SOS Showing on My iPhone?
If SOS is showing on your iPhone, it indicates that your device’s Emergency SOS feature has been activated. This feature is designed to quickly call for help in emergencies. When facing the SOS display on your iPhone, it is essential to understand how to use this feature effectively and responsibly.Continue Reading














![Ways To Find Lost AirPods [Step-by-Step Guide] 21 Lost AirPods](https://tech-review.com/wp-content/uploads/2024/09/Lost-AirPods.jpg)